 |
Cisco access list tutorial : The access control lists (ACLs), access list Cisco allow a router to permit or deny packets based on a variety of criteria access list cisco. The ACL is configured in global mode , but it applies at the interface. An access list cisco ACL does not take effect until it is applied specifically to interface with the IP access-group command . Packets can be filtered when entering or leaving an interface.
If a packet enters or exits an interface with an access list cisco ACL applied, the packet is compared with the criteria of the access list cisco ACL. If the packet matches the first access list cisco ACL line , the "permission " or appropriate action "deny" is taken. If no match is found , we examined the criterion of the second line. Again, if there is a match, that you take appropriate action if a match is found , the third line of the access list cisco ACL compared with the package.
This approach continues until a match is found , when the access list cisco ACL fails. If there is no match, a default " deny" is carried out , and the package will not be processed . When configuring an ACL , if not expressly allowed a packet, it will be subject to the implicit denial of the arrival of each access list cisco ACL . This is the default behavior of an access list cisco ACL and can not be changed .
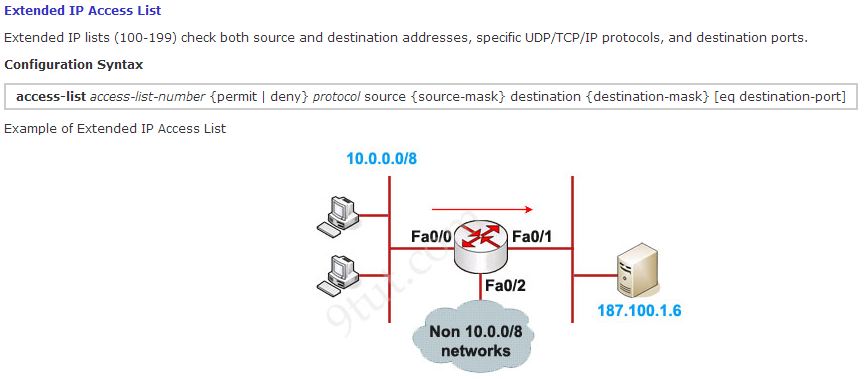
A standard ACL is concerned with a single factor, the supply of IP packets . The receiver is not considered . Extended ACL provide for each source and the location of the package , and can take into account the port number too. The numerical range used for each is different: Regular use 1-99 access control list ACL ranges from 1300 to 1399 and the lineups used 100-199 and 2000-2699 .
There are several points worth repeating before beginning to configure common access control list ACL .
access list cisco ACL Common considering only the IP address must match .
access list cisco ACL lines that run from floor. If there is no match on the line, the second is executed if no match in the second, third runs , and so on until there is a match , or the finish of the access control list ACL is reached . This process at the bottom of the first plan gives special value in the order lines .
There is an implicit deny at the end of each access list cisco ACL . If packets are not expressly authorized , are implicitly denied.
. If the Ethernet interface of Router 3 must accept only packets with a supply network 172.12.12 , the access control list ACL is configured as follows :
R3#conf t
R3(config)#access-list 5 permit 172.12.12. …255
The access list cisco ACL consists of one special express line allows packets to IP address 172.12.12. / 24 offer. The implicit deny this is not configured or realized in the configuration service , refuse all packets that do not match the first line.
The ACL is then applied to the ethernet0 :
R3#conf t
R3(config)#interface e0
R3(config-if)#ip access-group 5 in
But before creating the access control list ACL , this is a very good idea to see what other ACL is already running on the router ! To see the ACL that runs on the router , use the show access-list command, cisco access list tutorial :
R1#show access-list
Standard IP access list 1
permit …
Normal IP access list five
permit 172.1.1.1
Normal IP access list 7
permit 23.3.3.3
Extended IP access list 100
permit tcp any any lt www (26 matches)
permit tcp any any neq telnet (12 matches)
deny ip any any
Extended IP access list 105
deny tcp any any eq www
deny tcp any any eq telnet
You use the access list cisco ACLs all the way up the ladder of Cisco certification , and throughout his career. The value of knowing how to create and apply access control list ACLs is paramount, and it all starts with mastering the basics!



Aucun commentaire:
Enregistrer un commentaire